Venticento is a Qualys partner since 2016.
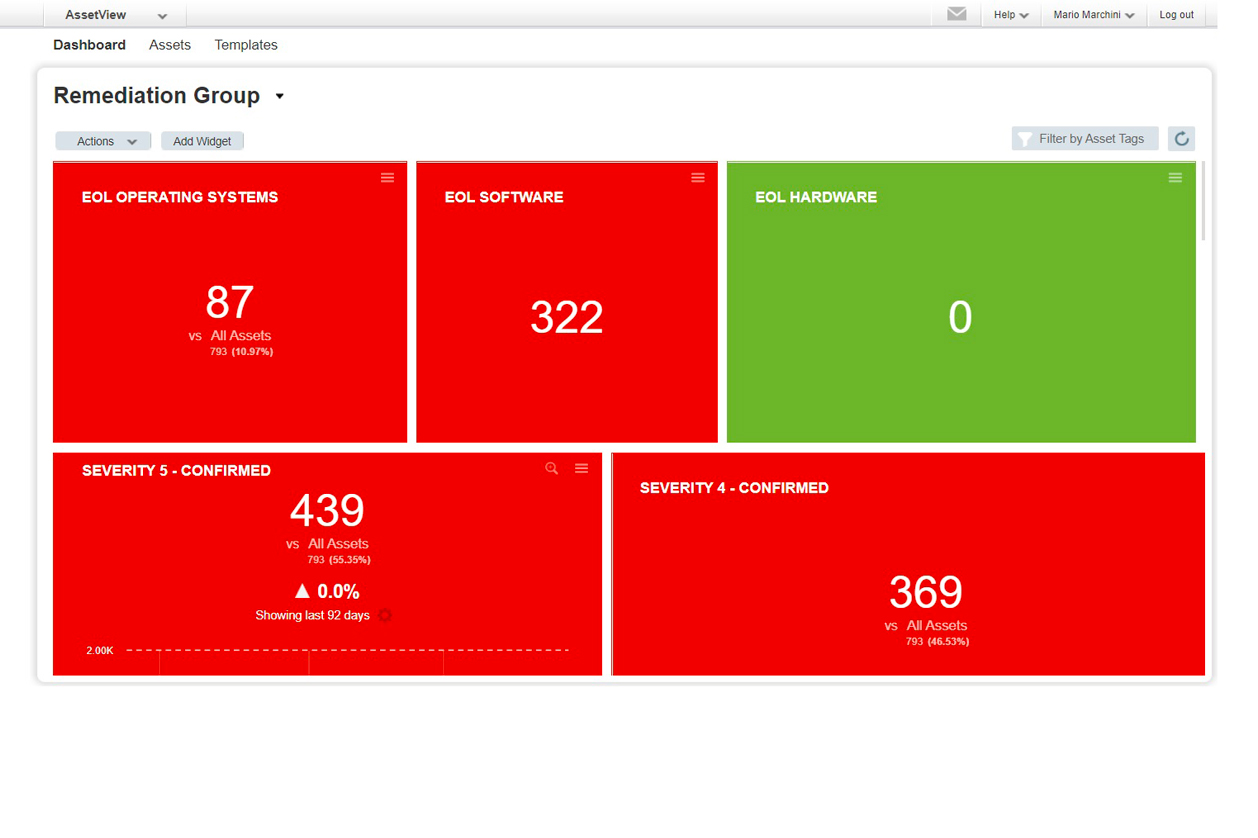
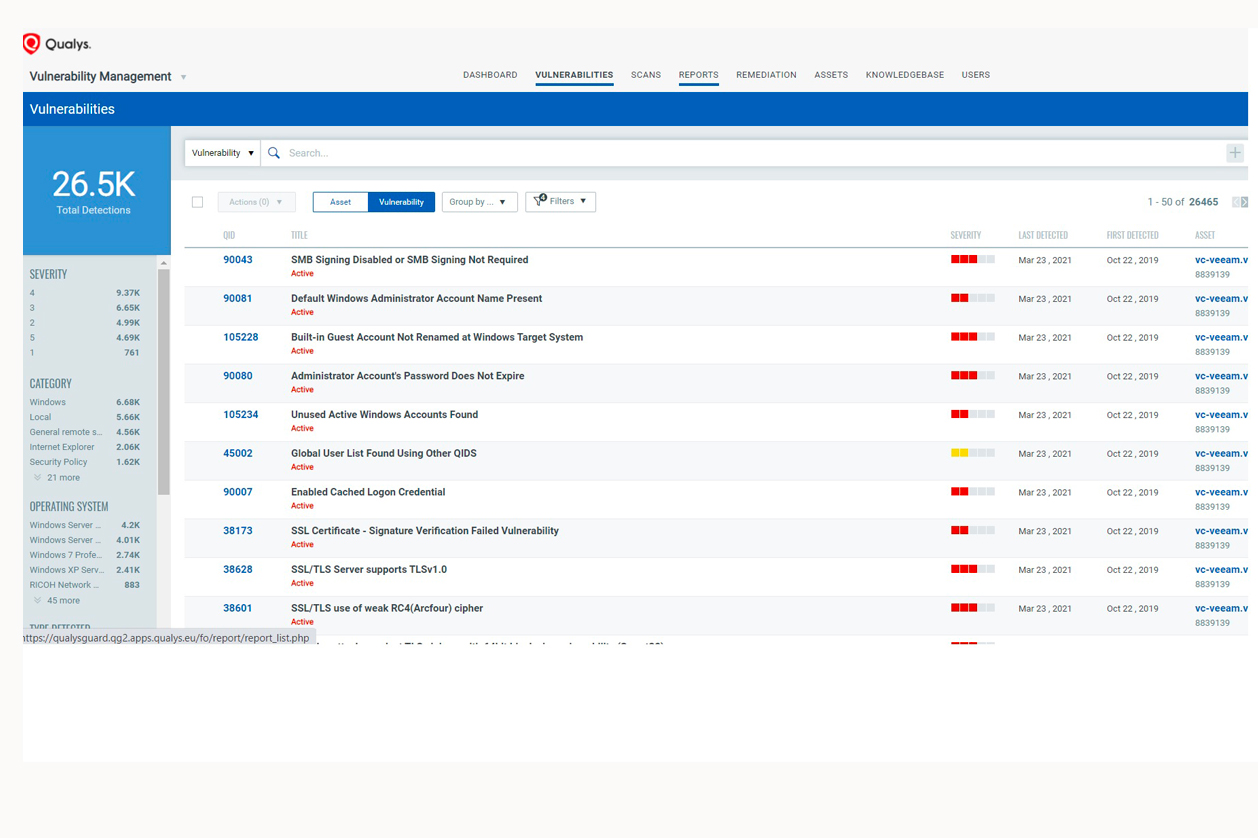
This solution allows us to identify the vulnerabilities present in the systems and networks of our customers and act promptly in the remedy limiting the possibility of hacker attack.
In addition, we use this tool to check corporate compliance related to privacy and data protection laws.
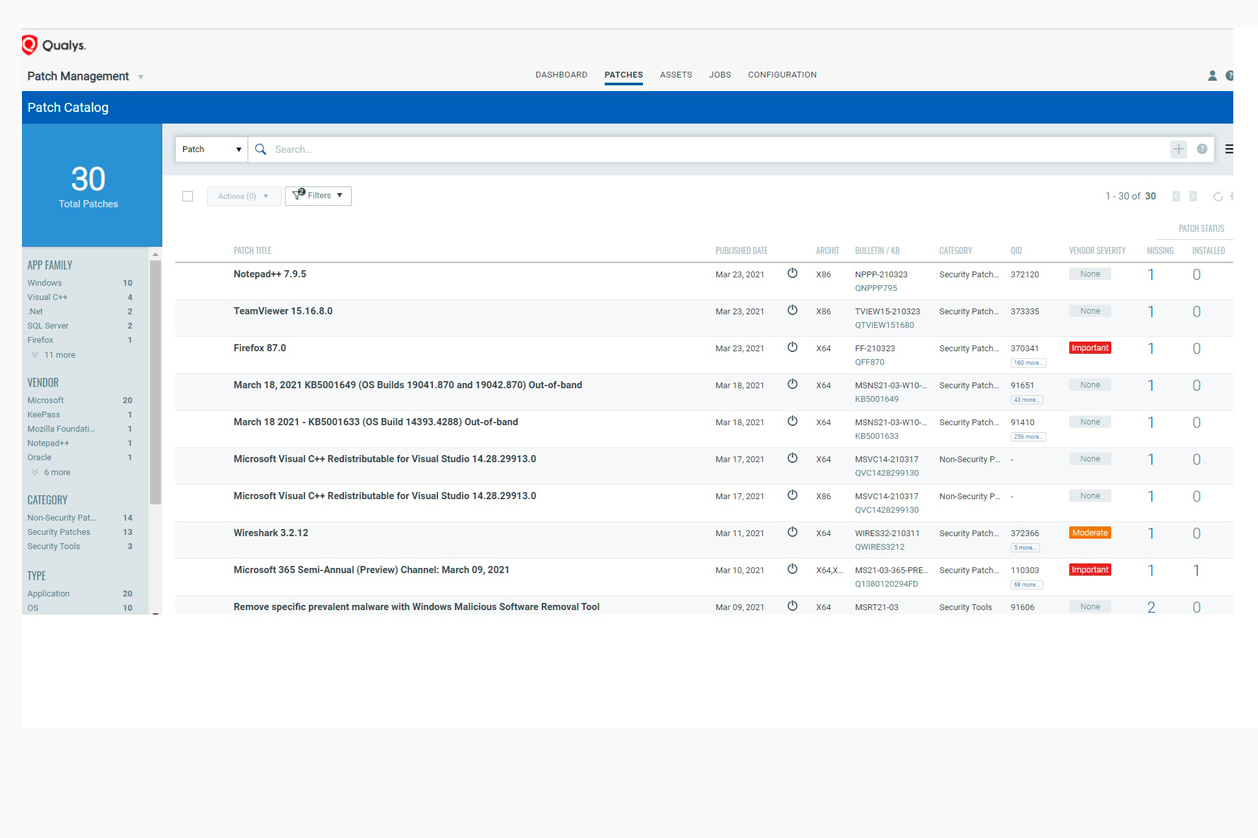
Our service also extends to the subsequent correction of vulnerabilities and the bringing into compliance with all system and design aspects detected anomalous.
Following are some of Qualys modules with the optional management services provided by out team:
Policy Compliance (PC)
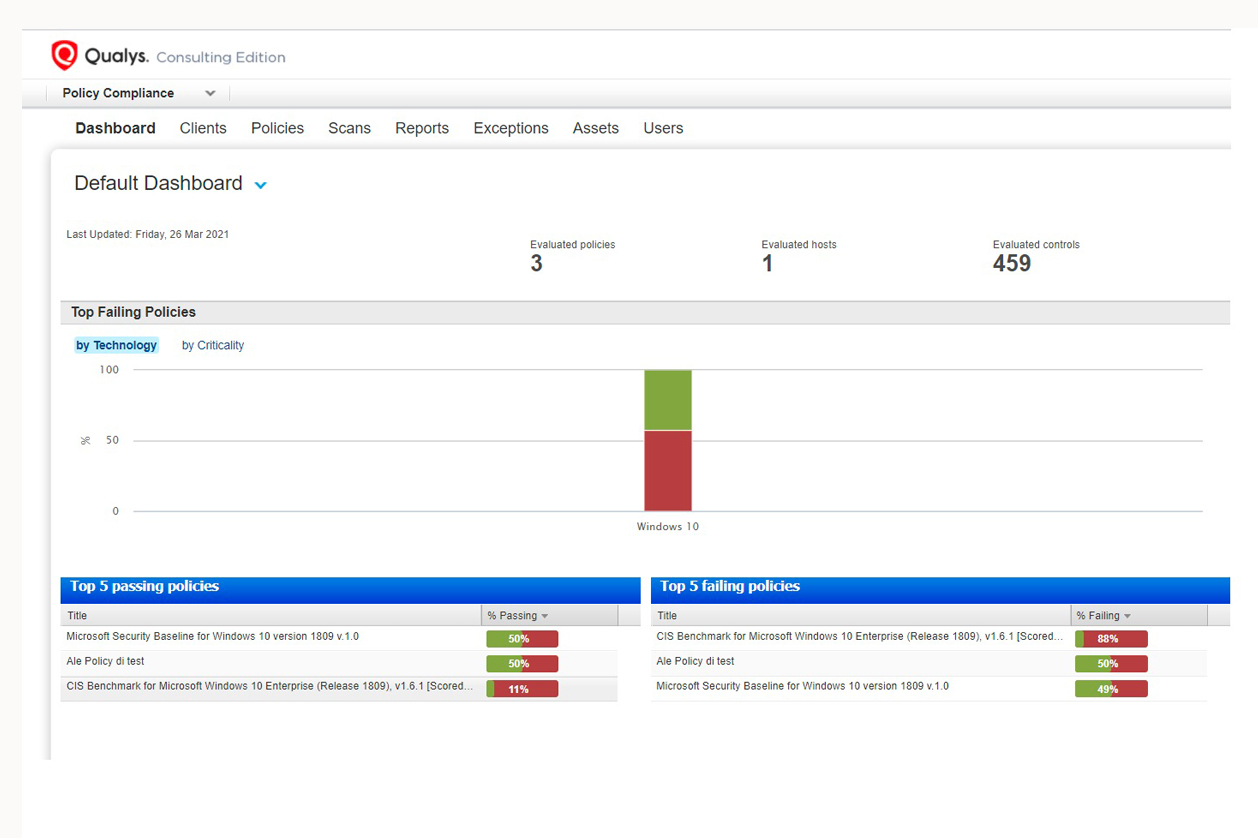
The Policy Compliance solution allows you to collect and analyze information relating to system configurations, correlating them with existing policies and regulations, in order to effectively document compliance with the rules. It is a fully automated system that helps reduce compliance management costs without necessarily requiring the use of agents.
Questionnaire (QS)
The Questionnaire is a service of immediate use but particularly powerful for automating the workflow. It includes the ability to centralize and automate risk assessment, collecting and archiving evidence from employees or partners, monitoring the progress of the assessment process.
Web Application Scanning (WAS)
The well-known and appreciated scalability of services Qualys WAS lets you continuously discover and catalog web apps in your network and detects vulnerabilities and misconfigurations.
Web Application Firewall (WAF)
Simple, scalable and adaptive, Qualys WAF blocks attacks, and lets you control when and where your applications are accessed. Qualys WAF and Qualys WAS work together seamlessly.
Qualys ThreatProtect (TP)
New vulnerabilities are discovered all the time, several thousand every year. However, not all vulnerabilities are identical: the correlation of intelligence information enriches the information that can be used to prioritize actions against vulnerabilities.